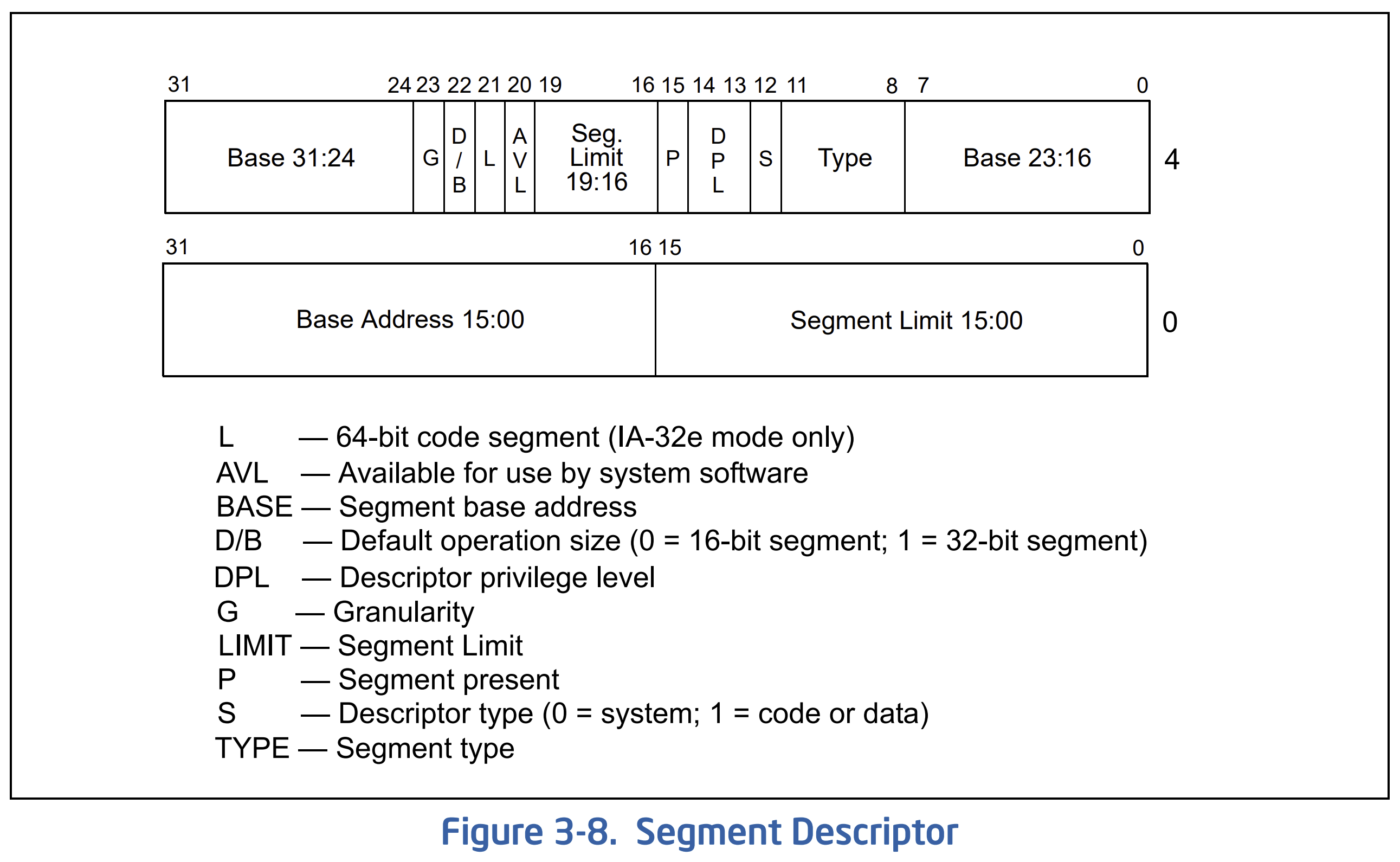
-
JTAG 'Hacking' the Original Xbox in 2023
Using Intel CPU JTAG to dump the secret bootrom in Microsoft's original Xbox
Released in November 2001, the original Xbox was Microsoft’s first venture into the game console industry. With its hardware closely resembling a cheap but versatile PC of the early 2000s, the device came under the immediate scrutiny of technical hobbyists looking to run ‘homebrew’ code and alternative operating systems on it.
Over the course of its lifetime, the Xbox was unilaterally hacked through a broad range of both hardware and software attacks. But at 20 years old, this Intel-based Pentium III system holds up as an amazing platform to learn or explore a plethora of security and computer systems engineering topics that are still relevant to this day.
As a fun departure from our usual content, this post exploits some nostalgia to tackle a challenge put forth by some of the earliest musings of the original Xbox researchers: “hacking” the original Xbox via Intel’s x86 CPU JTAG.
Continue Reading →
-
The LDT, a Perfect Home for All Your Kernel Payloads
Using the HIB segment to bypass KASLR on x86-based macOS
With the broad adoption of Kernel Address Space Layout Randomization (KASLR) by modern systems, obtaining an information leak is a necessary component of most privilege escalation exploits. This post will cover an implementation detail of XNU (the kernel used by Apple’s macOS) which can eliminate the need for a dedicated information leak vulnerability in many kernel exploits.
The key lies in the
__HIBsegment of the kernel Mach-O, containing a subset of functions and data structures for system hibernation and low-level CPU management, which is always mapped at a known address.We will first provide a general overview of the
__HIBsegment and the various ways that it can be abused. Using our Pwn2Own 2021 kernel exploit as a real-world example, we show how this exploit could be simplified to use the general techniques described here removing the need for its previously tedious leak construction.Continue Reading →
-
Exploiting Intel Graphics Kernel Extensions on macOS
A Pwn2Own 2021 Apple Safari Sandbox Escape
To escape the Safari sandbox for our Pwn2Own 2021 submission, we exploited a vulnerability in the Intel graphics acceleration kernel extensions (drivers) on macOS. This post will detail the bug and how we went about exploiting it to achieve reliable kernel code execution.
We delayed publishing this writeup as we discovered and reported a multitude of similar issues to Apple over the past year, the last of which was patched recently. With other researchers catching on, Intel graphics-related CVEs have become increasingly common among Apple’s security update listings. Quite recently, there was even an exploit discovered in-the-wild targeting the same Intel graphics kernel extensions discussed in this post.
Continue Reading →
Exploiting an Unbounded memcpy in Parallels Desktop
A Pwn2Own 2021 Guest-to-Host Virtualization Escape
What's New in Tenet v0.2
Quality-of-life improvements, cell-based trace visualization, and more...
Snapcraft Packages Come With Extra Baggage
Exploiting Ubuntu's Snapcraft Apps with CVE-2020-27348
All Your Base Are [Still] Belong To Us
Fuzzing Modern UDP Game Protocols With Snapshot-based Fuzzers
The Oddest Place You Will Ever Find PAC
Exploiting the notoriously unsafe gets() on a PAC-protected ARM64 binary
32 bits, 32 gigs, 1 click...
Exploitation of a JavaScriptCore WebAssembly Vulnerability
Tenet: A Trace Explorer for Reverse Engineers
Conventional Debuggers Are Crumbling to Software Complexity, Now What?
Lucid: An Interactive Hex-Rays Microcode Explorer
Studying decompiler internals has never been so easy...
7 Days to Lift: A Mission in Microcode
Extending the Hex-Rays Decompiler to Support Intel AVX Instructions
What's New in Lighthouse v0.9
Python 3, custom coverage formats, coverage cross-refs, themes & more
A Cryptocurrency Heist, Starring Your Web Browser
Abusing well-defined web standards to exploit localhost services
In Transactional Memory, No One Can Hear You Scream
Attacking Intel's Transactional Synchronization Extensions
What's New in Lighthouse v0.8
Binary Ninja support, HTML coverage reports, consistent styling
Scaling up Binary Exploitation Education
Augmenting Esoteric Security Subjects with Gamification & Accessibility
Exploiting the macOS WindowServer for root
Four Heap Sprays, Two Dangling Pointers, One Bitflip
Cracking the Walls of the Safari Sandbox
Fuzzing the macOS WindowServer for Exploitable Vulnerabilities
Weaponization of a JavaScriptCore Vulnerability
Illustrating the Progression of Advanced Exploit Primitives In Practice
Timeless Debugging of Complex Software
Root Cause Analysis of a Non-Deterministic JavaScriptCore Bug
Vulnerability Discovery Against Apple Safari
Evaluating Complex Software Targets for Exploitable Vulnerabilities
A Methodical Approach to Browser Exploitation
The Exploit Development Lifecycle, From A to Z(ero Day)
Building up from the Ethereum Bytecode
Practical Decompilation of Ethereum Smart Contracts
What's New in Lighthouse v0.7
Frida, C++ demangling, context menu, function prefixing, bugfixes
Dangers of the Decompiler
A Sampling of Anti-Decompilation Techniques
What's New in ripr v1.1
Function Arguments, Basic Block Mode, and more
Untangling Exotic Architectures with Binary Ninja
Supplementing Flare-On 2017 with some sanity
What's New in Lighthouse v0.6
Intel pintool, cyclomatic complexity, batch load, bugfixes
Hello World
Compiling Executables for the Classic POSIX Subsystem on Windows